Large-scale cyberattacks make the news, but that’s just the tip of the iceberg. Cybercrime is on the rise, and most attacks happen from phishing emails. Any fraudulent emails that demand you to reveal personal information such as a username and password, SSNs, or credit card numbers are known as phishing attacks.
There are different types of phishing:
- Spear Phishing/Whaling – is a highly focused phishing attack designed to target business executives or specific employees.
- Baiting – dropping malware-infected USB’s in common areas hoping that someone will pick it up and plug it in his/her computer.
- Email from Friend – In this phishing attack an attacker after successfully compromising a device can send malicious emails to the friends in the address list of the compromised person.
- Pretexting – is a phishing attack where the attacker fakes a situation to lure you into giving valuable information.
More about Phishing:
Phishing attacks are now more sophisticated than ever and very tricky. Once compromised, the fraudulent email could deliver new malware, denial-of-service attacks, or ransomware.
Special Alert: Phishing is also the #1 method of ransomware attacks. Ransomware is a form of malware extortion software to encrypt and lock our files, then hold a ransom to pay to unlock the files. Purdue Systems Security have many security protection mechanisms in place including multi-factor authentication (MFA), but we need everyone more aware to protect Purdue University.
Here’s how to spot a phishing email:
- Provokes fear or urgency
- Asks you to click
- Uses vague language and generic greetings
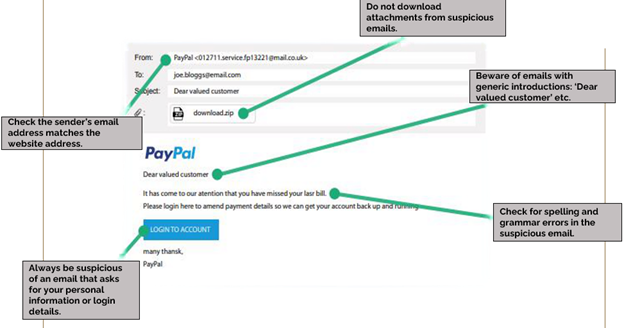
Know the warning signs of a phishing attack: Does the sender's address match the website address? Is it asking for personal or login information? Be wary of attachments, generic introductions, and spelling and grammatical mistakes - all are signs of potential phishing.
PSS Cybersecurity Awareness Tips!
- Avoid clicking links or downloading attachments without verifying the mail's source and the sender very carefully.
- Check all links and attachments rigorously, and never click or open any that seem suspicious.
- Analyze any requests for personal or university information.
- Always be weary of any messages demanding that you take immediate action. Don't react instinctively and always verify the request's authenticity.
Be very cautious of any unexpected messages, especially if the content seems suspicious or too good to be true, as they usually are.
How can you help prevent the spread of phishing messages?
- Understand what to look for in a malicious message (uses threats or a sense of urgency, asks for credentials, or asks for you to buy something).
- Forward the email as an attachment to abuse@purdue.edu.
To learn more about Purdue’s Cybersecurity Awareness, visit https://www.purdue.edu/securepurdue/Cybersecurity/index.php or email Nolyn Johnson at cyberaware@purdue.edu.
Last updated: 11/18/2022

